Cryptography has changed since it was first conceptualized. It dates back to Ancient Egypt and has since become very relevant today. No longer is cryptography just used in the military or to hide clever ciphers into riddles; it has become a staple of security today in modern-day encryption technology.
But how did this come to be? How did encryption come out of the study of encoding messages? You’ll see in this essay how cryptography came out from the tombs of Ancient Egypt, traveled across the globe, even helped determine the outcomes of WWII, and soon became the present-day tool we heavily rely on to keep our computers safe.
Early Days of Cryptography
The purpose of cryptography in the early days was simply to conceal information. Codes and ciphers have been used for the military, in places of political strife, and to safely archive dangerous information. The most well-known instance was with the German Enigma, which we’ll discuss later.
The history of cryptography all starts in Ancient Egypt, where a particular scribe used strange hieroglyphs instead of the usual ones. However, this purpose was to make the writing more dignified. But it did lay the basic groundwork for cryptography in the future.
Then in India, the ‘Arthshastra’ – an ancient work on politics and government – describes an ancient espionage service that gave orders to its members in “secret writing.” More evidence of cryptography in ancient times.
Also, the ancient Greeks were said to have known about cryptography, and they used scytales and transposition ciphers together to encrypt information. The Greek historian Polybius even made the Polybius Square.
Simple Ciphers
The Ancient Greeks used scytales, the transposition cipher, and the Polybius square (discussed later). Scytales and a transposition cipher are fundamentally simple. The transposition cipher works by scrambling the plaintext (the message) into a random way that can still be deciphered, and a scytale is a tool in conjunction with a transposition cipher to explain a message. (Image found here on Wikimedia Commons)
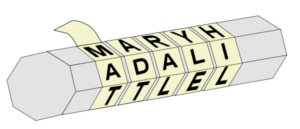
The Polybius Square is also simple enough to understand. The numbers are coordinates to a space on the square, and you would go to that space on the square. I and J share a square in the modern alphabet, and the Greek version 5,5 on the square would denote a space or the end of a sentence.

Monoalphabetic ciphers: What are they? Monoalphabetic ciphers are about as simple as you get, using only one alphabet for the cipher. Change this number for this letter, and you’re good, or something along those lines.
Now by one alphabet, what do I mean? Someone could layer on another cipher, making it harder to crack. Say we do something. And then, after finishing that, we put on the Polybius Square.
The reason why these were easy to crack was 1) it’s a simple substitution cipher and 2) using letter frequencies. But what is it? Well, letter frequency is how often a letter appears in a language. This was how letters in Scrabble were given point values – by how often they appeared in words. (Image can be found here)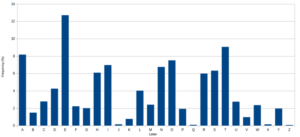
Cryptography in the Middle Ages
At about 1000 B.C., Julius Caesar used his Caesar cipher (a substitution cipher) to convey information to his generals on the frontlines. It worked by simply taking the letters of the message you wanted to encrypt and moving six letters forward. It was a simple yet great start in the right direction.
Caesar’s military made use of ciphers too. This was to make it difficult for information to be decoded if the wrong files were to fall into the wrong hands. Many plans and conspiracies and communications were encoded by the military, especially during World War 2.
Now modern cryptology, as it stands, might have originated in Arabia. First, there was Al-Khalil, who wrote the Book of Cryptography Messages, which listed the permutations of all Arabic words without vowels. Then Al-Kindi stepped in and invented frequency analysis for breaking substitution ciphers when he wrote the Manuscript for the Deciphering Cryptographic Messages.
In the meanwhile, scribes in England were using ciphers to hide things in their prose and riddles, adding to the complexity and challenge of solving them. These ciphers also added to the sophistication of riddles.
Then, in Italy, the French cryptographer Vigenere designed a cipher that was supposedly the first one with an encryption key. It added the message letter and the encryption key letter mod 26 – basically taking the letter value of the message’s letter (C = 3, being the 3rd letter of the alphabet) and taking the letter value of the encryption key’s letter (H = 8) and added them together (11), divided 26 by the sum and took the remainder (4 = D).
The substitution ciphers – the simplest form of ciphers – and yet the most widely used – work by interchanging letters with numbers (with the numbers denoting the letter’s place in the alphabet). This means A = 1, B = 2, and so on. This is the easiest cipher decryption/encryption.
Cryptography in the Wars
Fast forward to the start of the 19th century, everything became electric. The inventor Edward Hebern invented his Hebern rotor machine. It was a device that hid the cipher key in a rotating disc, which hid a substitution cipher in it and would change every time – it was broken by using letter frequencies (how often letters show up in words).
Then the Enigma showed up in Germany, based on Hebern’s rotor machine, except it used 3-4 rotors instead of one that all rotated at different rates. The Enigma was soon counteracted by the Polish, who sent the technology to decrypt Enigma’s work over to the Brits, who used it to get the daily key. This allowed the Allies to get valuable information to assist their attempts to take down the Axis by intercepting naval messages and decrypting them to take control of the seas, for one thing.
Cryptography in the Modern Times
Today, digital encryption works by two users having a private key and a public key. The specifics are complex, but suffice it to say that this method of encryption is reliable enough for modern-day consumers.
In a nutshell, a person has a private and a public key. The public key can be combined with another private key to encrypt something, and the private key and a public key can be used to decrypt something and send a message back.
In conclusion, I would like to state that cryptography definitely is no longer the same as it was back in Ancient Egypt. Not only that but also the ability to make your information and data private has proven to be of significance, especially in the world of today.
Now, cryptography is defined by Wikipedia as the practice of using secure communication against adversarial behavior. Here, adversarial means those who would want to undo the cipher. So cryptography is all about concealing information and securing it safely. This effort to hide and conceal information to the naked eye has always been about privacy and safety, and it’s the whole purpose of digital encryption today.
These days, cryptography’s use is more or less the same – conceal information within lines of code and secure data from hackers.
About the Author

James Trayton is 14 years old. He’s in Grade 9. He loves to eat Blueberry Cheese Cake. During his free time, you’d catch him playing D&D, writing, programming, Worldbuilding, or watching cartoons. He’s a BUBOTS Writing Academy advanced level student.

